In Part 1, we gave an overview of the growth of stegware (steganography malware) and how security experts underestimate its use as an attack vector. In this blog we look at the ways stealthy stegware is delivered and how this dangerous threat can be so difficult to detect.
In its simplest form, stegware is concealed inside seemingly innocuous digital images. In the burgeoning digital era, cyber attackers used the increasingly multimedia-driven content of the internet to their advantage to conceal their secret code within public images.
As the digital era progressed, cyber attackers deployed new techniques in which to disguise their malicious code. Network steganography became more widely used, taking advantage of the ephemeral nature of network channels.
However, the most popular, and simplest, technique used by attackers is to hide code in the least significant bits (LSB) of an image, such as within the colours of pixels. For example, manipulation of the last bits of the RGB channels in a digital image produces such a slight change in colour that the human eye is unlikely to detect the difference. That makes it an ideal vehicle for an attacker who can hide coded commands in the images that users unsuspectingly download onto their system. This technique is depicted in Figure 1.
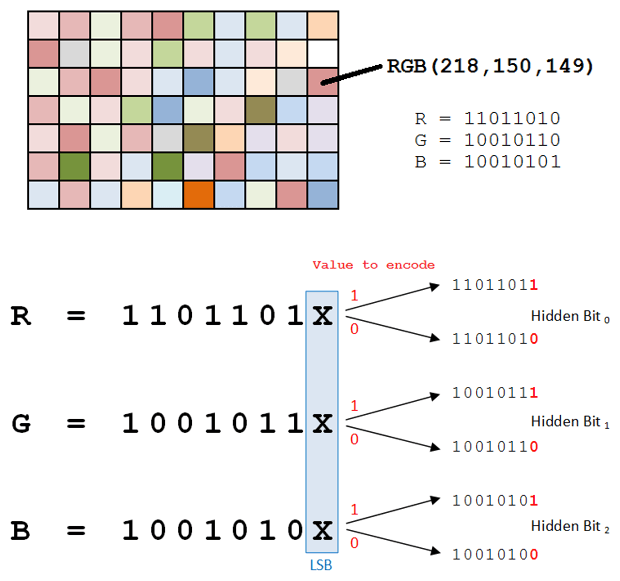
Malware authors continue to enhance their capabilities by finding new ways to transport secret code as testified by the emergence of Stegoloader, a modular version of digital steganography. This first came to light in 2015 when a form of malware known as Win32/Gatak.DR was found to have been concealed in a PNG file that had been downloaded from a legitimate website.
The modular capacity of this stegware signalled a significant development in steganography techniques concealed in digital images. Attackers could now monitor the environment of the malware, optimize the timing of its launch to prevent detection, check for compromised systems and to deploy other modules, if required. This type of technique has evolved further with variants found that launch the Vundo malware family, which installs adware, ransomware and scareware. Another variation includes the malicious code of the VeryMal malvertising campaign that sends unsuspecting infected users to the veryyield-malyst domain . It was calculated to have yielded over $1.2m in just one day.
The focus of SIMARGL’s research in this area is to develop a solution based on open source steganalysis tools for detecting LSB steganography in images. This will enable existing tools to more easily be integrated into SIMARGL’s partners’ products.
The focus of SIMARGL’s Group 2 definition is on malware that modifies a digital image file’s structure. An example of this is the ZeusVM malware, a spin-off of the Zeus banking trojan, which has been found in JPEG images. The principle follows that of the infamous Hammertoss APT where well-established practices are combined into a multi-staged attack with an image used to transport the code to a file that is modified to communicate with the C&C server. This is depicted in Figure 2 where an innocent JPEG, in this case showing a sunset, is downloaded from the C&C server:
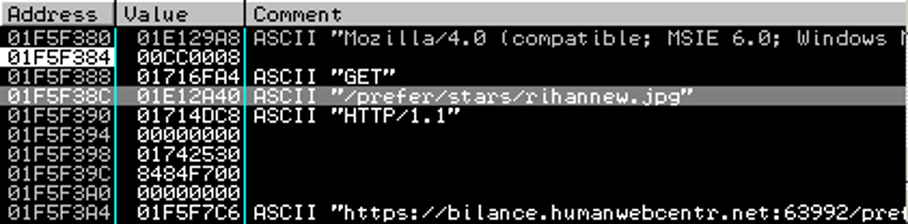
The malware config file is appended after the original image data and the image still launches correctly as shown in Figure 3:

There is a plethora of information hiding techniques that can be utilized for covert communication by modern malware authors who are adept at toning their skills as required. There are many more sophisticated techniques that can be envisioned, and many that already exist, that malware developers may soon be able to use to their advantage.
At the moment, the complexity and sophistication of the methods currently used is still quite low which is why now is the right time to react by developing effective countermeasures to limit the impact.
Keep an eye on the SIMARGL blog where we will expand upon this stegware primer with more advanced techniques and countermeasures that SIMARGL will utilize.
This blog post is published by CUING as part of work on the SIMARGL project.